Passwords are one of the most prominent security tools used today. A concept introduced all the way back in 1961 by computer scientist Fernando Corbato, passwords have been keeping devices safe and secure for decades. However, due to their protective and secret nature, passwords are […]
Blog
A new cybersecurity threat has recently come to light in which hackers use reCAPTCHA to trick users into infecting their devices with malware. If you aren’t already aware, reCAPTCHA is a service powered by Google that protects websites from spam and abuse by detecting and […]
Remote Desktop Protocol, or RDP, is a protocol that allows users to access and control a computer remotely, or over a network connection. Using this protocol, you can connect to a computer that is located elsewhere, such as an office. Many people utilize this protocol […]
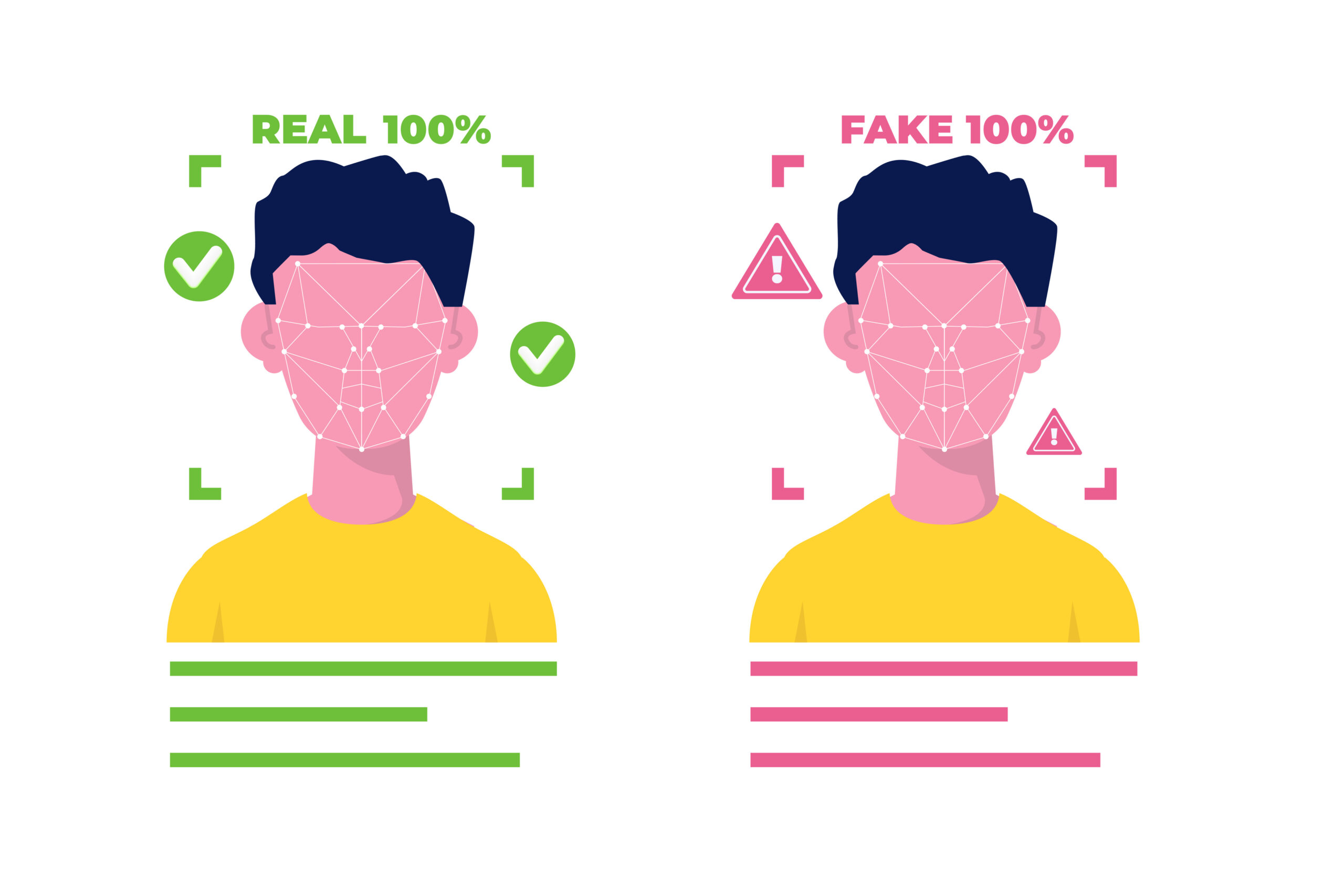
In the last year, nearly half of businesses observed a steep increase in generative-AI or deepfake related scams. Even before AI, scammers have attempted and successfully committed cyberattacks by impersonating real people. Usually, a scammer will obtain the personal information of a trusted employee and […]
Every day, companies around the world continue to improve their individual AI software programs. If you’ve been online recently, you have probably noticed that AI seems to be almost everywhere, from your Facebook feed to your iPhone messages, and that presence has grown rapidly over […]
Within a business, certain accounts in a network are often given more privileges than others, meaning they can complete tasks or access files that other accounts are not able to. For example, a business owner’s account will probably have more permissions, via an admin log […]
At various times throughout your workday, you may find yourself needing to double-click your mouse while completing certain actions on your computer. Some of the most common uses of the double-click include opening files on your device, opening applications, or highlighting text. This action is […]
Most software companies regularly send out software updates for their products in order to continuously provide a trustworthy, valuable service. Software updates are typically necessary to keep applications and devices running smoothly as technology changes, and can also provide improved or updated features, fix previously […]
Purchasing a used computer can be a great, budget-friendly option when it comes to obtaining devices for your company. Overall, used computers are cheaper than their brand-new counterparts, have less environmental impact since the materials are being reused instead of thrown away, and can be […]